Do you think your
Document are safe?
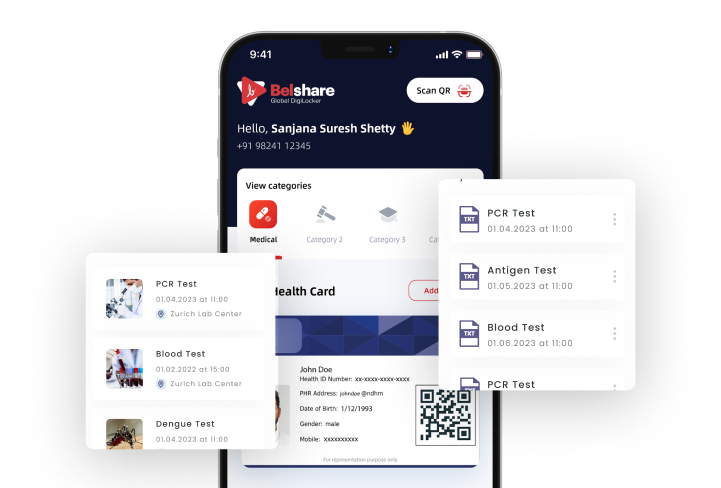
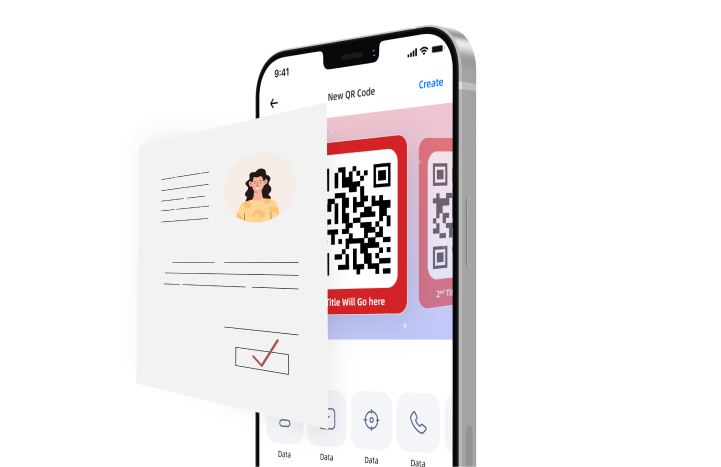
Identity life cycle management system now more secure with BELRIUM BLOCKCHAIN
Integration of milestone 1(M1 License) is completed by BelfricsBT & the Belshare application is approved by the National Health Authority of India. The blockchain based Belshare application will soon be available for Indian citizens to generate ABHA health IDs. Belshare is built over the identity-oriented Belrium blockchain. You will soon be able to experience the revolution and manage your IDs safely and securely.